Configuring the Identity Management Service communication settings
📘 Instructions
To configure the communication settings to allow PrinterOn to authenticate against your third-party identity management service:
On the Authentication tab, select Third-Party Identity Management Service as your Authentication method. The Third-Party Identity Management Service panels appear.
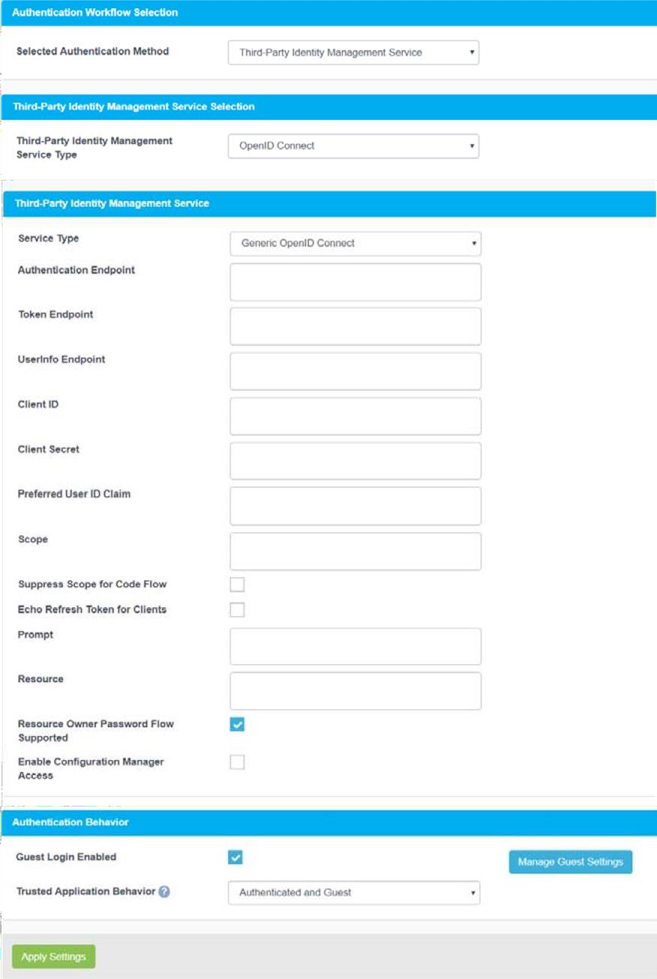
In the Third-Party Identity Management Service panel, configure the communication settings as necessary.
Configuring the Identity Management Service communication settings | Service-Type
Configuring the Identity Management Service communication settings | Authentication-Endpoint
Configuring the Identity Management Service communication settings | Token-Endpoint
Configuring the Identity Management Service communication settings | User-Information-Endpoint
Configuring the Identity Management Service communication settings | Client-ID
Configuring the Identity Management Service communication settings | Client-Secret
Configuring the Identity Management Service communication settings | Scope
Configuring the Identity Management Service communication settings | Suppress-Scope-for-Code-Flow
Service Type
Specify the specific OpenID variant used by the IDM.
For most IDMs, you should select Generic OpenID Connect.
If you are using the Google Identity Platform, select Google OpenID Connect.
Note: Google Identity Platform is not a fully supported IDM; however, it is currently in Beta.
Authentication Endpoint
The URL hosted by the Identity Management Service to which the PrinterOn server redirects the user for authentication.
If the user is successfully authenticated, the Identity Management Service returns an authorization code to PrinterOn, which informs the PrinterOn service that the user has successfully authenticated and is authorized to access the PrinterOn service.
Token Endpoint
The URL hosted by the IDM from which the PrinterOn server requests Access, ID, and Refresh tokens. The PrinterOn Server uses these tokens to determine the authentication status of the user.
If the credentials have expired, the user is forced to reauthenticate.
User Information Endpoint
The URL where PrinterOn can access user profile information, such as their email address. PrinterOn downloads this user data to the PrinterOn user store the first time a user logs in.
Client ID
The unique ID of the PrinterOn service is generated when you register PrinterOn with your IDM. Depending on the service you are using, this value may be automatically generated by the IDM, or you may enter your Client ID value.
The PrinterOn Server requires this value to authenticate with the IDM.
Client Secret
The unique client secret key for your PrinterOn service. You must generate this key in your IDM and copy the value to this field.
The PrinterOn Server requires this value to authenticate with the IDM.
Preferred User ID Claim (Advanced view only)
The identifying information that PrinterOn requires from the user when authenticating against the IDM. This value is optional.
If you define a value for this field (for example email address), then users would be required to supply that value to be authenticated.
If you leave this field blank, by default PrinterOn requires the Preferred Username claim from the user to authenticate them.
Scope
The scope of information collected about a user during authentication, such as their email, username, and so on.
In almost all cases, you should set Scope to a value of openid email profile offline_access. This value permits PrinterOn to collect only the minimum necessary user information required.
Suppress Scope for Code Flow
When checked, the scope is not passed on when the PrinterOn server requests a refresh token for the user.
Because the user has previously been authorized with a specified scope, the scope is unnecessary for the IDM to issue a refresh token. Most IDMs simply ignore the scope of any refresh request. However, some IDMs will reject a refresh request if it includes scope values, essentially revoking authorization for the user. In these cases, you can enable this setting to prevent the PrinterOn server from including the scope in the refresh request.
Echo Refresh Token for Clients (Advanced view only)
When checked, the PrinterOn server returns the refresh token that was included in a refresh request.
Before performing a time-intensive task, the PrinterOn server preemptively submits a refresh request, to ensure that the user’s authorization remains valid for the duration of the task. In most cases, IDMs either issue a new refresh token to the PrinterOn server or return the same refresh token. The PrinterOn server then returns the response to the client app that made the request.
However, some IDMs do not return any token if the provided refresh token is still valid. This can cause issues for some client apps, since the apps may expect a refresh token in the response. To mitigate any issues that may occur in such a scenario, you can check this setting to ensure that the client app receives the expected token in the response.
Prompt (Advanced view only)
A message PrinterOn displays to the user to allow them to grant permission for PrinterOn to authenticate them.
Some Authentication services require a user’s consent to allow PrinterOn access to the service on their behalf. This message will be used to prompt the user for confirmation when necessary.
Resource (Advanced view only)
The resources or APIs that are being authorized for use. Typically, this field can be left blank.
Resource Owner Password Flow Supported
When checked, the IDM allows PrinterOn to collect the user password and pass it on to the Identity Management Service, instead of redirecting the user to the Authentication URL to supply their credentials.
Enable Configuration Manager Access
When enabled, allows users to log into the configuration manager by authenticating against the Identity Management Service.
In the Authentication Behavior panel, configure the following settings as necessary:
Guest Login Enabled: When enabled, specifies that unauthenticated users are permitted to print. When guest login is enabled, you must also configure guest identification and designate one or more printers as guest printers. For more information, see Configuring guest printing.
Trusted Application Behavior (Advanced view only): Defines the minimum authentication requirements for users printing through the Print Delivery Gateway (PDG) using the Google Cloud Print workflow. For more information, see Configuring authentication requirements for Google Cloud Print users.
Click Apply Settings.
You can now access the Users tab to create user groups and Access Control Rules. For more information, see Managing the PrinterOn user store.
